AgriDataValue adopts a DevSecOps approach for development, integration, testing and deployment.
The integration framework and tools are covered in this blog post, along with an indication of which ones AgriDataValue used to create the project’s CI/CD pipeline. Development, security, and operations, or DevSecOps, automate the integration of security at each stage of the software development lifecycle, from initial design through integration, testing, deployment, and software delivery [1].
The term “DevSecOps” suggests that security is integrated into the Agile and DevOps practices that development organizations adopt. Instead of relying on Quality Assurance (QA) testing at the end of the development cycle, on production, security issues are addressed as they arise in this viewpoint. Therefore, by automating the delivery of secure software without slowing the software development cycle, DevSecOps speeds up both the software development and release cycles.
The best practices for DevSecOps, as identified by IBM in July 2020 [1] may be summarized as follows:
- Shift left: It encourages integrating security into all processes from software development to delivery from the start and moving security from the right, or the end of the DevOps process, to the left. Particularly, early involvement of cybersecurity experts in the design, development, and validation processes can help to implement security as software components are constructed. In the early stages of the software lifecycle, security risks and vulnerabilities can then be discovered and properly addressed.
- Security education: To achieve the intersection of engineering and compliance with an organization’s security measures, software engineers must receive security training. The terms threat models, compliance checks, vulnerability tests, and implementing security controls should be understood by developers.
- Culture: The implementation of DevSecOps requires a culture of security within organizations or even teams because it will enable people to comprehend and carry out their responsibilities in the DevSecOps lifecycle. In fact, the culture of security will involve people, communication, processes, and technology so that the chosen technological tools and the necessary software security are integrated into organizational processes.
- Traceability, auditability, and visibility: These principles should serve as a guide for companies adopting DevSecOps in order to ensure greater insight into a more secure environment. Tracking configuration items that are well documented and distributed appropriately within the company will make it easier for DevSecOps to function there.
DevSecOps, as approached in AgriDataValue, is illustrated in Figure 1. According to the figure, this DevSecOps approach has the following stages: “Plan,” “Create,” “Verify,” “Package,” “Release,” “Configure,” “Detect,” “Respond,” “Predict,” and “Adapt.” These stages are correlated in a continuous workflow.
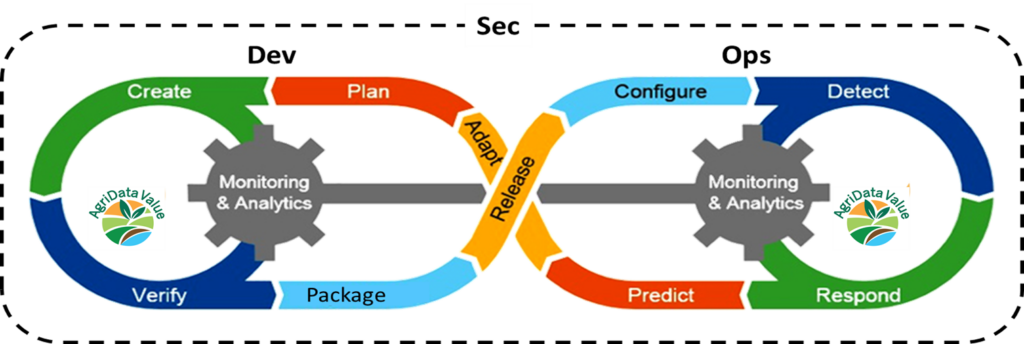
The terms “Plan” and “Create” refer to the design and development of software, respectively. The terms “Verify”, “Package,” and “Release” refer to Continuous Integration and Continuous Delivery, which are handled by automated CI/CD tools, specifically GitLab in AgriDataValue. The remaining steps of the “Ops” section deal with production-level QA testing and the procedures for relaying their results back to the design and development phases in a continuous, circular interaction. Monitoring and analytics tools will make it possible to properly log throughout the entire software lifecycle during the DevOps process. Last but not least, security is integrated into every step of this DevOps cycle, implementing security by design across the individuals, teams, and technologies involved in the creation and release of the AgriDataValue software.
[1] IBM Cloud Education, „DevSecOps,“ IBM, 30 07 2020. [Online]. Available: https://www.ibm.com/cloud/learn/devsecops


